Chamd5圣诞节礼物
初探
- 下载压缩包,得到一堆exe,直接运行没看到东西,strings了一下,发现是python打包成的exe,调用先解exe,再反编译pyc,得到源码,这里随便贴其中一个
import hashlib
import base64
from Crypto.Cipher import AES
from Crypto import Random
def decrypt(data, password):
bs = AES.block_size
if len(data) <= bs:
return data
unpad = lambda s: s[0:-ord(s[-1])]
iv = data[:bs]
cipher = AES.new(password, AES.MODE_CBC, iv)
data = unpad(cipher.decrypt(data[bs:]))
return data
encrypt_data = '......'
md5 = hashlib.md5()
fn = raw_input()
md5.update(fn)
if '10fb15c77258a991b0028080a64fb42d' == md5.hexdigest():
print 'Are you robot?'
print '87 + 20 = ?'
ans = int(raw_input())
if int(ans) == 107:
try:
md5 = hashlib.md5()
inp = str(int(ans))
md5.update(inp)
password = md5.hexdigest()
encrypt_data = base64.b64decode(encrypt_data)
decrypt_data = decrypt(encrypt_data, password)
f = open(fn, 'wb')
f.write(decrypt_data)
f.close()
except:
pass- 把前面的md5和算术题去掉,运行,能得到一个图片,上面有一小点字母或者数字,代码最顶上注释有第几个,大概就是拼起来吧
写脚本
解包
- 改了下 pyinstxtractor.py,这里贴部分代码
def main(argv):
arch = PyInstArchive(argv)
if arch.open():
if arch.checkFile():
if arch.getCArchiveInfo():
arch.parseTOC()
arch.extractFiles()
arch.close()
print('[*] Successfully extracted pyinstaller archive: {0}'.format(argv))
print('')
print('You can now use a python decompiler on the pyc files within the extracted directory')
return
arch.close()
if __name__ == '__main__':
path = r'E:\BaiduNetdiskDownload\quiz'
li = os.listdir(r'E:\BaiduNetdiskDownload\quiz')
for l in li:
if l.endswith('exe'):
main(r'E:\BaiduNetdiskDownload\quiz' + '\\' + l)
补头
import os
li = os.listdir(r'./')
print(li)
for l in li:
if l.endswith('exe_extracted'):
ll = os.listdir('./' + l)
bt = b'\x03\xf3\r\npyi0'
with open('./' + l + '/' + ll[0], 'rb+') as f:
so = f.read()
with open('./' + ll[0]+'.pyc', 'wb+') as f:
f.write(bt)
f.write(so)反编译pyc
- 直接用的图形化的 EasyPythonDecompiler.exe,省事
提取encrypt_data和算术题答案
- 暴力了一点,这里是python2
import os
import hashlib
import base64
from Crypto.Cipher import AES
from Crypto import Random
def decrypt(data, password):
bs = AES.block_size
if len(data) <= bs:
return data
unpad = lambda s: s[0:-ord(s[-1])]
iv = data[:bs]
cipher = AES.new(password, AES.MODE_CBC, iv)
data = unpad(cipher.decrypt(data[bs:]))
return data
path=r'./output'
for i in range(1,60):
with open(path+'/'+str(i)+'.pyc_dis') as f:
s=f.read()
# print()
md5 = hashlib.md5()
inp = str(eval(s.split('\'')[7][:-3]))
md5.update(inp)
password = md5.hexdigest()
encrypt_data = base64.b64decode(s.split('\'')[1])
decrypt_data = decrypt(encrypt_data, password)
f = open(path+'/'+str(i)+'.png', 'w')
f.write(decrypt_data)
f.write('\n')
f.close()
拼接图片
from PIL import Image
image_white = Image.new('RGB', (2400, 100), 0xFFFFFF)
posx = 0
for i in range(1, 60):
im = Image.open(r'E:\BaiduNetdiskDownload\png' + '\\' + str(i) + '.png')
image_white.paste(im, (posx, 0))
posx += im.width
image_white.save('./result.png')
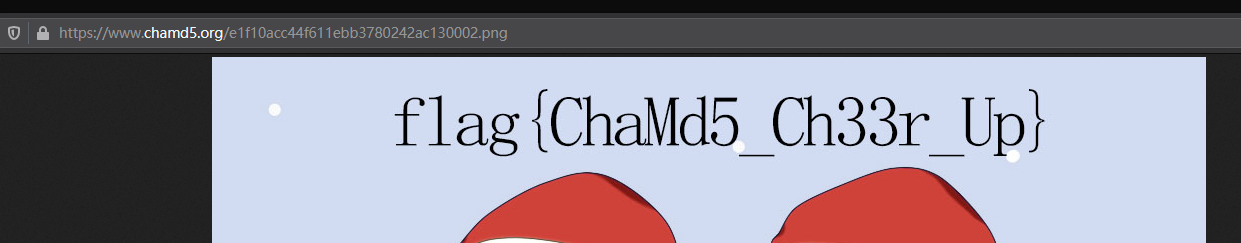
image_white.show()读网址
读了半天,一直错了,甚至让我一直以为套娃了个web题,要打那个Gh0st1.0网站,扫了半天目录,看了半天源码- 仔细拼了一下出来图片了
- https://www.chamd5.org/e1f10acc44f611ebb3780242ac130002.png
后记
最后得了个水杯和一件卫衣(优秀wp),真舒服