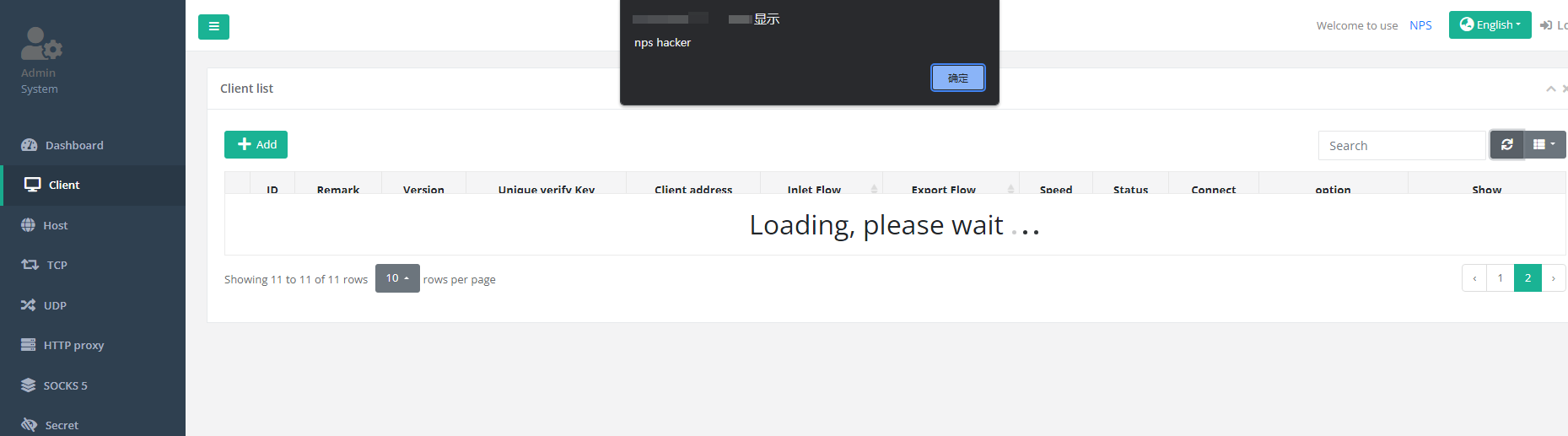
nps console XSS vulnerability CVE-2023-46486
Environment setup
Project address https://github.com/ehang-io/nps
Cause of vulnerability
bootstrapTable is not configured with the escape field, plus the nps wrong user default configuration file
Affected product
nps<=0.26.10
Description
An XSS vulnerability was discovered in nps<=v0.26.10. An attacker can connect to the server by using a malicious client npc, and eventually form an XSS vulnerability in the web console of nps.
Principle analysis
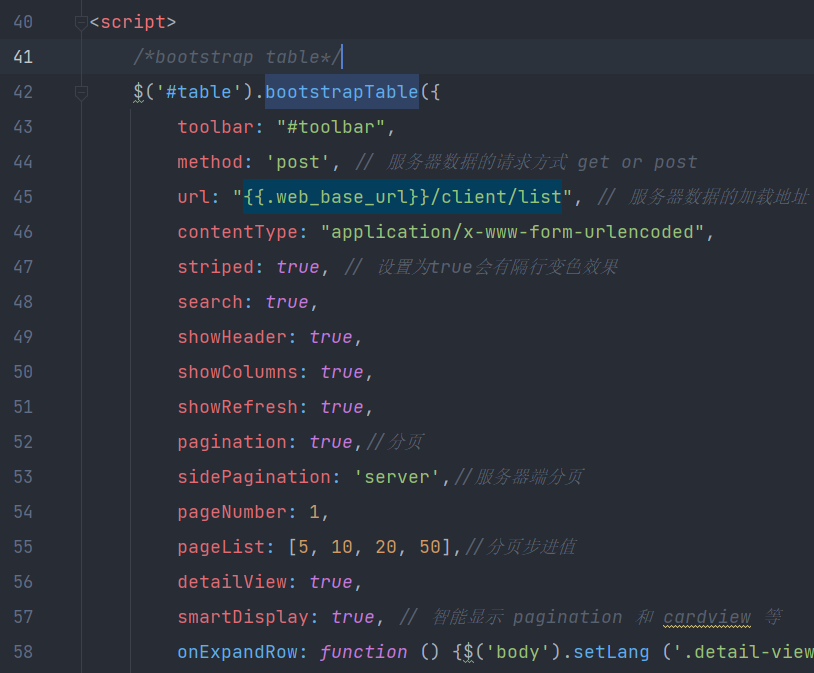
The page template web/views/client/list.html:42 is not configured with escape: true
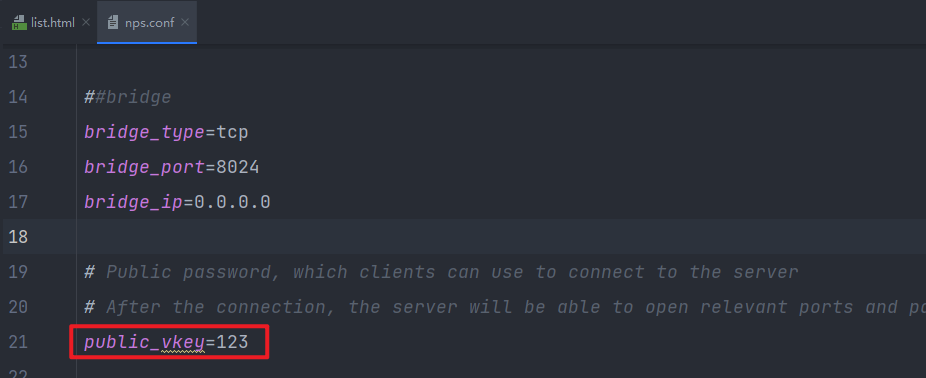
The conf\nps.conf configuration file is configured with public_vkey=123 by default
The attacker uses public_vkey as a client to connect to nps, and can configure username, password, notes and other information. The bootstrapTable of the web console does not escape these characters, eventually forming an XSS vulnerability.
nps控制台XSS漏洞 CVE-2023-46486
环境搭建
项目地址 https://github.com/ehang-io/nps
漏洞成因
bootstrapTable并未配置escape字段,再加上nps错误的用户默认配置文件
影响范围
nps<=V0.26.10
修复办法
将web/views中的页面文件中的所有bootstrapTable配置中加入escape: true
修改public_vkey
原理分析
页面模板 web/views/client/list.html:42 中并未配置 escape: true

conf\nps.conf 配置文件默认配置有public_vkey=123

攻击者使用public_vkey作为客户端连接至nps,并可配置用户名、密码、备注等信息,web控制台的bootstrapTable并未转义这些字符,最终形成XSS漏洞
POC
使用如下配置文件
[common]
server_addr=127.0.0.1:8024
conn_type=tcp
vkey=123
remark=<sCRiPt>alert(`nps hacker`)</sCrIpT>使用如下命令连接
npc -config npc.conf打开控制台即可弹窗